Background
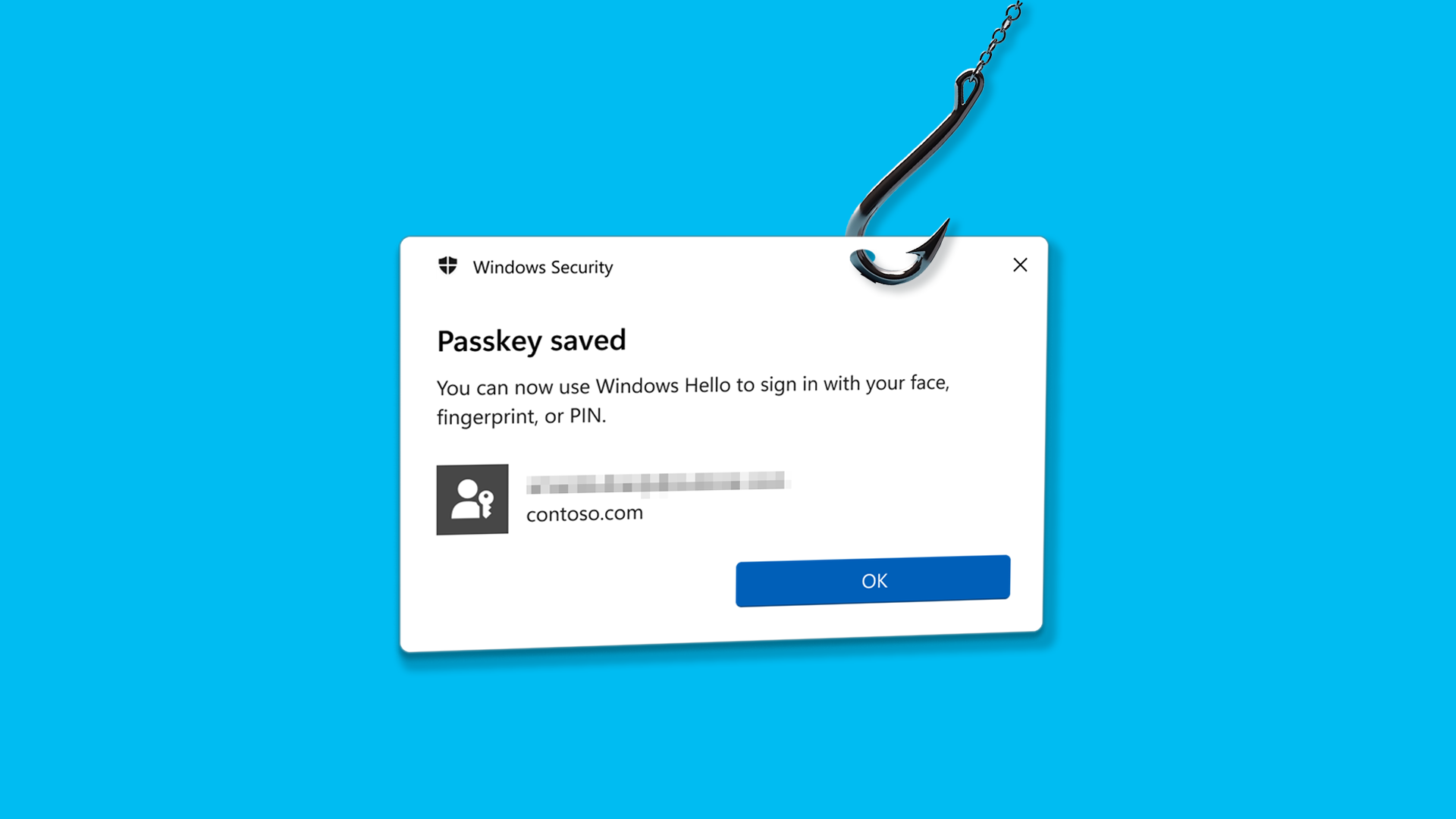
On the night of 24 March 2025, a client received an email from their lawyer requesting them to review an important document. The email appeared legitimate, complete with the lawyer’s real email signature, which added to its authenticity. The client, expecting paperwork, clicked the link and attempted to log in using a Face ID passkey, as prompted by a fake Microsoft 365 login page. However, they quickly became suspicious and contacted our emergency after-hours support line, a crucial step that ultimately saved them from a potentially disastrous breach.
How the Attack Worked
The attack was sophisticated and leveraged a compromised email account belonging to the lawyer. This allowed the attackers to send phishing emails that looked authentic, as they included the lawyer’s real email signature. The attackers created a fake Microsoft 365 login page that prompted the client to use Face ID or a passkey for login, bypassing traditional password entry. Instead of stealing a password, the attackers stole a valid session token, enabling them to access the real account without multi-factor authentication (MFA) or a password. The attackers were moments away from setting up persistent access by registering new trusted devices, creating app passwords to bypass security checks, and installing OAuth applications to maintain long-term access.
What We Did
Upon receiving the client’s call, our team immediately sprang into action. We forced an immediate logout of all active sessions to kick out the attacker, ensuring that no unauthorized access was maintained. Next, we revoked all authentication tokens to prevent session hijacking, which would have allowed the attackers to continue accessing the account even after the initial login. We then scanned for and removed any unauthorized OAuth apps or app passwords that the attackers might have installed. To further secure the account, we locked it down and enforced additional security measures. Finally, we contacted the law firm to notify them of the compromise and prevent further attacks, ensuring that their email account was secured to prevent similar incidents in the future.
Outcome
Thanks to our swift intervention, we prevented the attackers from establishing persistent access to the client’s account. The client’s data remained secure, and we ensured that no unauthorized access was granted. Our actions also helped protect the law firm from potential future attacks by alerting them to the compromised email account. This successful intervention highlights the importance of having a responsive and proactive cybersecurity team that can act quickly in emergency situations.
Why traditional security tools failed
Traditional security tools failed to detect this attack for several reasons. Since no password was stolen, there were no password alerts triggered by the phishing detection systems. Additionally, because passkeys skip MFA, there were no SMS codes or push notifications to warn the user of suspicious activity. The email came from a legitimate but compromised account, making it difficult for phishing filters to block. Finally, the login appeared as a valid Face ID or passkey approval from the user’s real device, which IT tools saw as normal behavior, further complicating detection.
Recommendations for protection
To protect against similar attacks, it is crucial to train employees to be cautious of passkey and Face ID logins, even when they appear to come from trusted senders. Verifying the domain before approving any login request is also essential.
Using security keys like YubiKeys can prevent token theft by ensuring that only authorized devices can access accounts.
Monitoring OAuth permissions and removing unnecessary third-party app access can also help prevent attackers from maintaining long-term access.
Finally, implementing conditional access policies to restrict logins based on location, device, or behavior can provide an additional layer of security against sophisticated phishing attacks.
Conclusion
While Microsoft has emphasized that passkeys are phishing-resistant, the rapidly evolving nature of cyber threats underscores the critical need for vigilance and swift response. This case study illustrates the importance of proactive security measures and 24/7 support in preventing potentially disastrous breaches.
Our emergency support team’s rapid intervention highlights the value of combining effective security tools with a responsive support team to bolster defenses against sophisticated phishing attacks. By adopting this approach, businesses can significantly enhance their security posture in today’s dynamic threat landscape.
